Cloud asset governance
Currently, this feature is behind the feature flag CCM_ENABLE_CLOUD_ASSET_GOVERNANCE_UI. Contact Harness Support to enable the feature.
The Harness cloud asset governance platform enables you to achieve a highly managed cloud environment using a Governance-as-Code approach that includes real-time enforcement and auto-remediation capabilities. The platform operates through a set of rules, which are in a YAML configuration file, and focuses on cost optimization. Harness Cloud Asset Governance provides tools to optimize your cloud spending and avoid unnecessary costs.
The platform is built on top of Cloud Custodian, an open-source project that is incubated by the Cloud Native Computing Foundation (CNCF).
Governance-as-Code is a modern approach that enables organizations to automate and manage various aspects of cloud governance using code. It utilizes software versioning, declarative programming languages, and automation mechanisms to synthesize cloud policies into a cloud-specific language that is implemented through a YAML configuration file.
At a high level, Cloud Custodian integrates seamlessly with services, features, and resources native to AWS, Azure, and GCP. The platform's basic syntax of resources, filters, and actions eliminates the complexity of API calls, business logic, and data translation, making cloud policy authorship more straightforward and efficient.
Harness supports only AWS cloud governance in its initial release.
Anatomy of a cloud asset governance rule
Cloud policies use a declarative vocabulary of resources, filters, and actions to be configured in YAML. This vocabulary is explained in the table below:
| YAML Key | Description |
| policy | A Cloud Custodian policy is defined in YAML format and consists of a set of filters and actions that are applied to a specific type of AWS resource. |
| resource | In Cloud Custodian, a cloud resource or service (such as ASG, S3, EC2, ELBs, RDS, etc.) is referred to as a "key" in a policy file. This key specifies the type of cloud resource or service that the following actions and filters act upon. Go to Cloud Custodian documentation for more information. |
| filters | In Cloud Custodian, filters are criteria that are used to narrow down resources based on their attributes. These attributes include tags, metadata, or other resource properties. The result of a filter is an output of resources that meet the criteria specified in the filter. This output is then used as the input for the actions defined in the policy. Filters in Cloud Custodian are essentially key-value pairs that can also be used more generically. They allow users to specify conditions that must be met for a resource to be included in the output. Go to Cloud Custodian documentation for more information. |
| actions | In Cloud Custodian, actions are operations that can be performed on a resource and are applied to the output of the filters specified in the policy. Actions can include things like terminating an EC2 instance, deleting an S3 bucket, or sending an email notification. Actions in Cloud Custodian are essentially webhooks that are executed when the criteria specified in the policy are met. These webhooks can also be used more generically, allowing the automation of a wide range of tasks. |
Here’s an example of a cloud asset governance policy to migrate your Amazon EBS volumes from gp2 to gp3 and save up to 20% on costs:
policies:
- name: migrate-gp2-to-gp3-ebs-volumes
resource: ebs
filters:
- VolumeType: gp2
- modifyable
actions:
- type: modify
volume-type: gp3
AWS access permissions
Enable the following permissions in AWS to execute cloud governance rules:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"ec2:Describe*",
"ec2:DeleteSnapshot",
"ec2:DeleteVolume",
"ec2:Get*",
"ec2:ListImagesInRecycleBin",
"ec2:ListSnapshotsInRecycleBin",
"elasticbeanstalk:Check*",
"elasticbeanstalk:Describe*",
"elasticbeanstalk:List*",
"elasticbeanstalk:Request*",
"elasticbeanstalk:Retrieve*",
"elasticbeanstalk:Validate*",
"elasticloadbalancing:Describe*",
"rds:Describe*",
"rds:List*",
"autoscaling-plans:Describe*",
"autoscaling-plans:GetScalingPlanResourceForecastData",
"autoscaling:Describe*",
"autoscaling:GetPredictiveScalingForecast",
"s3:DescribeJob",
"s3:Get*",
"s3:List*"
],
"Resource": "*",
"Effect": "Allow"
}
]
}
- This is not an exhaustive list; you may require additional permissions to support custom rules.
- A yellow underline in a custom policy indicates that you need permission to support the underlined filters and/or actions.
Add permissions
If you come across an error message indicating missing permissions, as displayed in the following screenshot, you need to add the missing permission here.
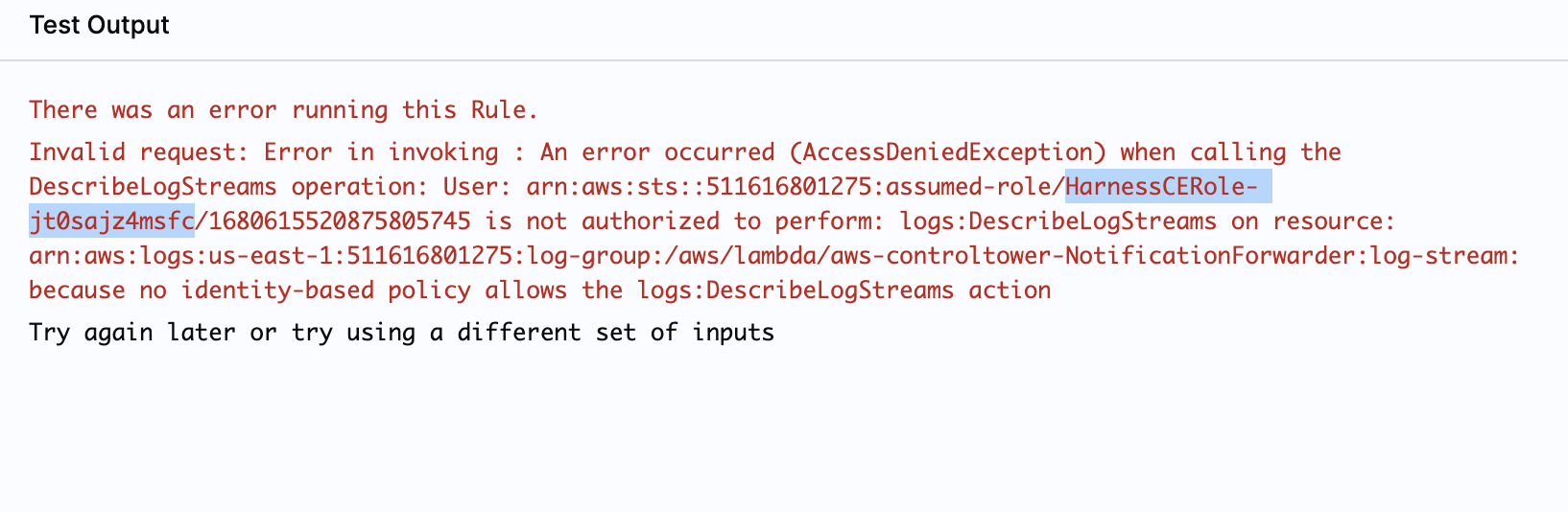
Copy the role specified in the error message that requires permission to execute the rule.
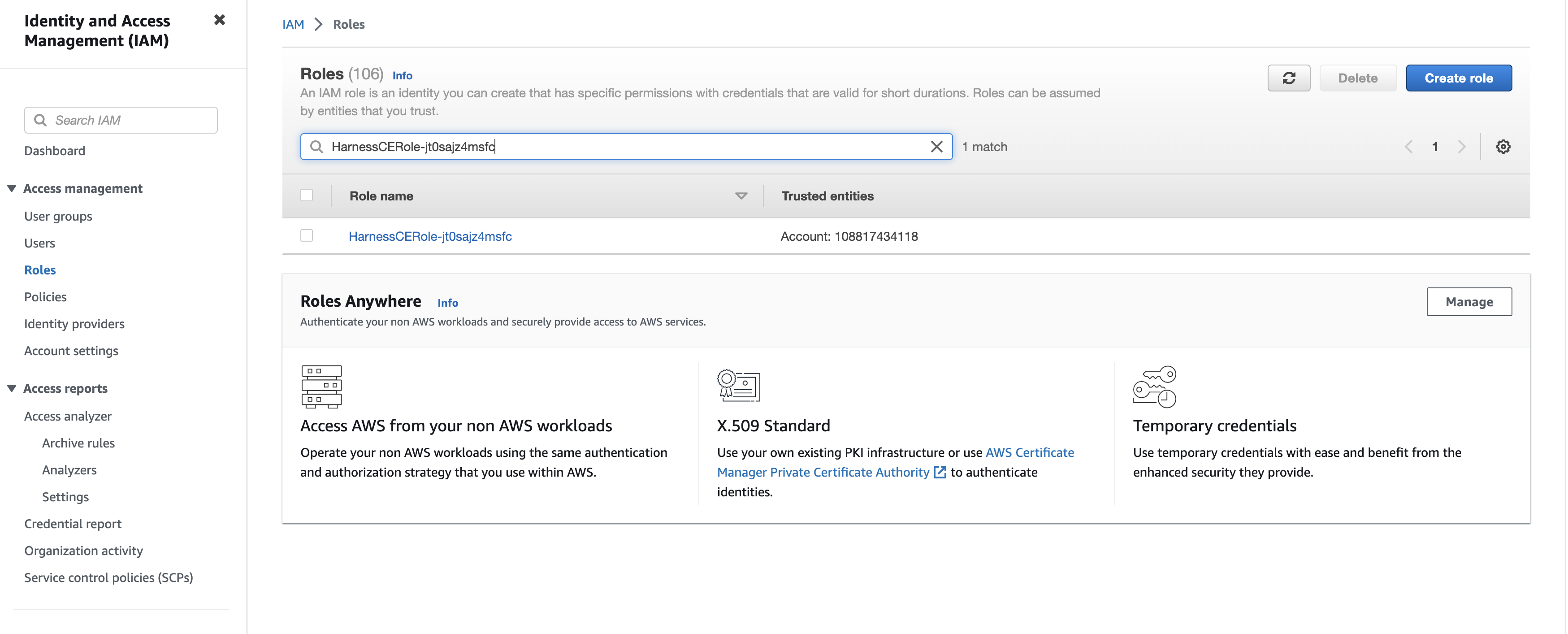
Enter the role in the search text box in IAM > Roles to filter the roles. The policies are displayed.
In the list of policies, select the policy to edit.
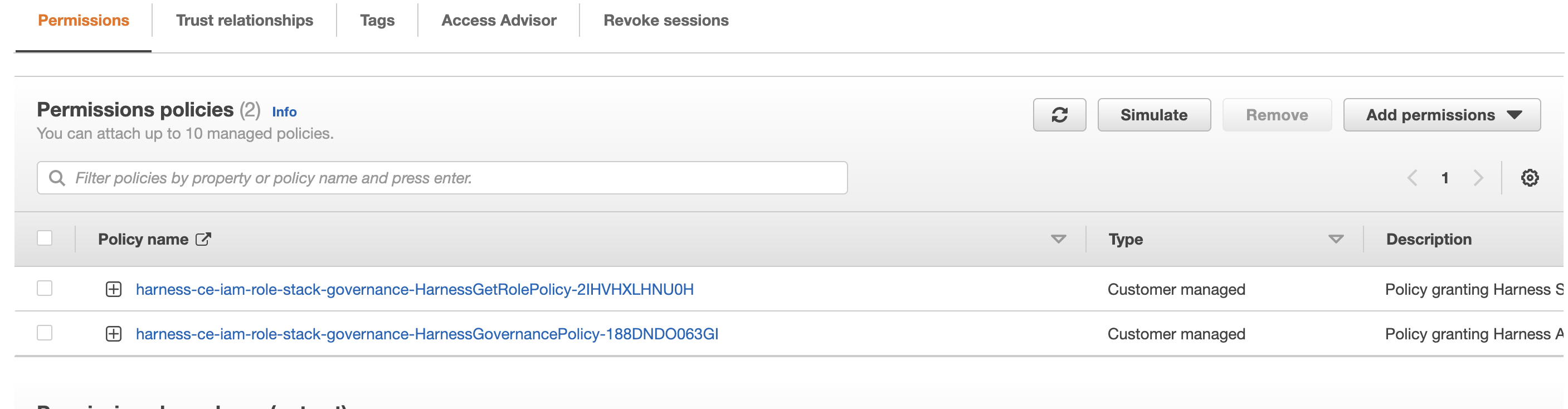
In the Permissions tab, select Edit policy, and then go to the JSON tab.
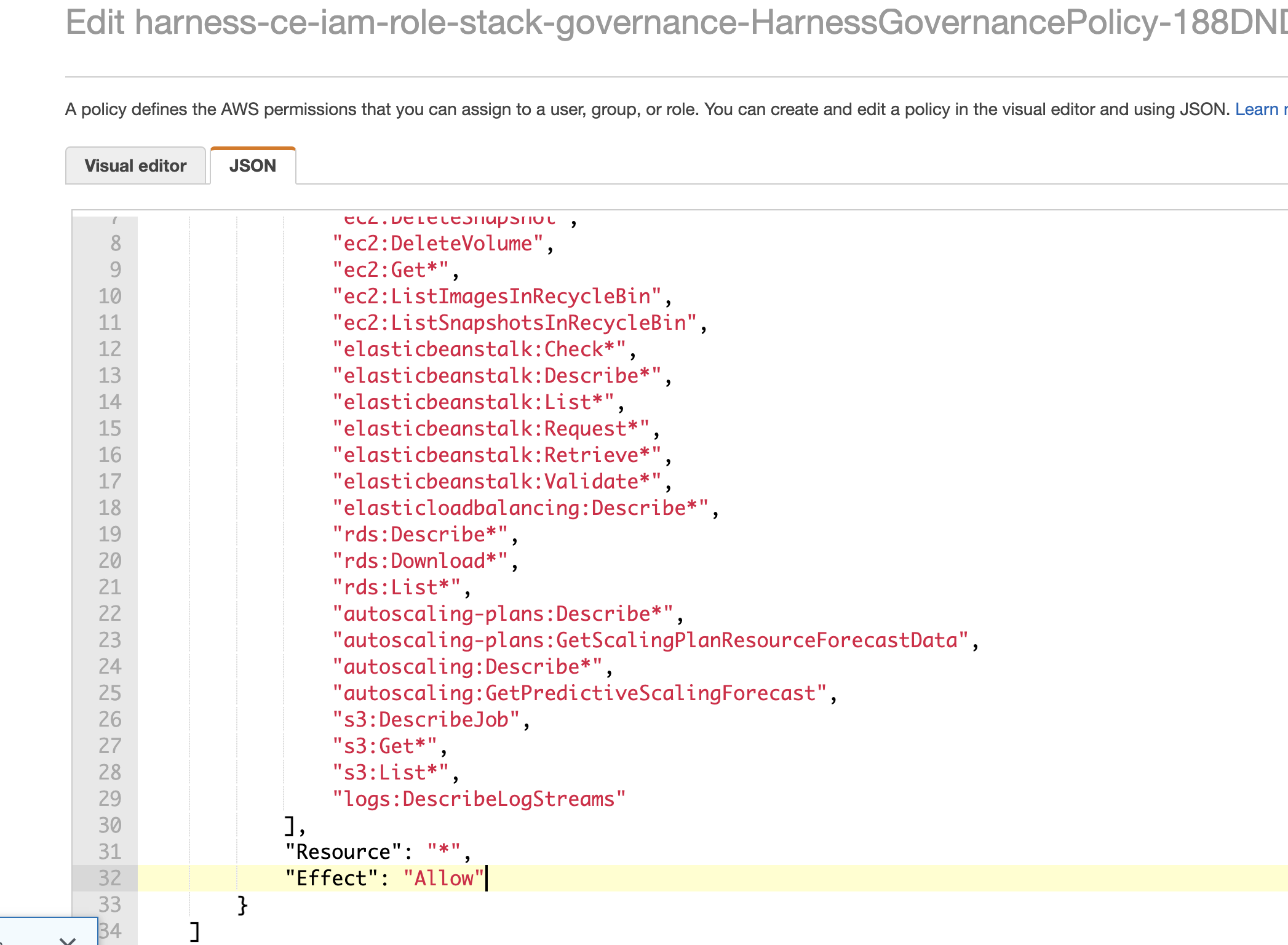
Add the missing permissions. You can use a wildcard (asterisk) to grant multiple permissions. For example,
s3:Get*permission would allow multiple S3 actions that start with "Get".Save changes.
For more information, go to Editing IAM policies.