Role-based access control overview
Access management for resources is a critical function for your Accounts, Organizations, and Projects. Harness Role-Based Access Control (RBAC) helps you manage who has access to your Harness resources, what they can do with those resources, and in what scope they have access.
What is Harness Role-Based Access Control?
Harness RBAC is role-based. This means the permissions to resources are determined by the roles assigned to Users, User Groups, and Service Accounts.
For example, certain users may have permission to execute pipelines, whereas other users may have permission to view the pipelines but not execute them.
Harness RBAC is an authorization system that provides fine-grained access management of Harness resources.
This video provides a quick overview of how you can manage access to your resources using Harness RBAC.
Visual summary
Here is a quick overview of Harness RBAC:
- The Account Administrator invites Users to the Account.
- The Account Administrator creates User Groups.
- The Account Administrator creates Service Accounts.
- Role Assignments happen on individual Users, User Groups, or Service Accounts.
- Each User can be a member of multiple user groups and hence can have multiple role assignments.
- Each User Group and Service Account can have multiple role assignments.
- You can assign roles at any scope.
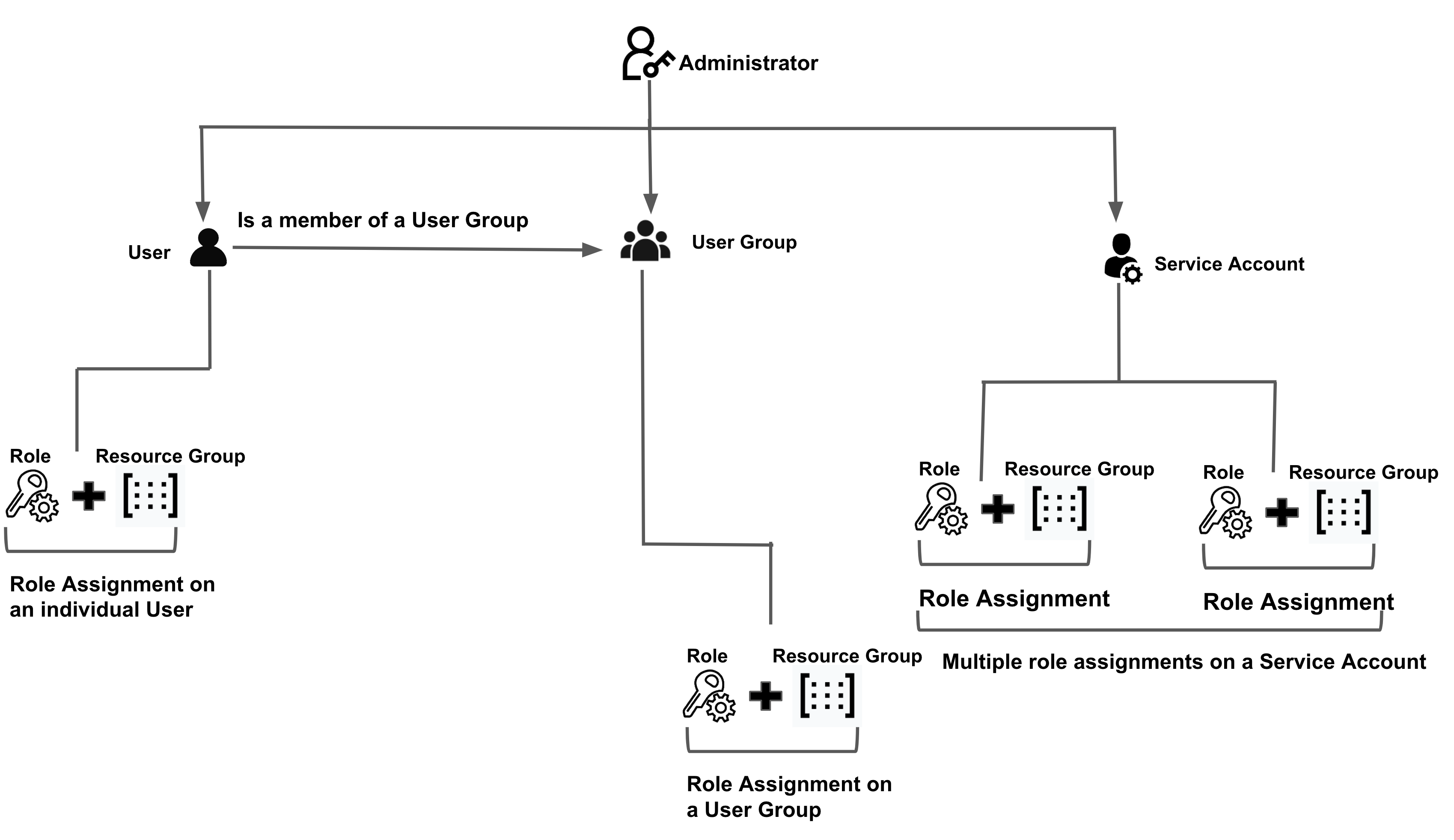
Harness RBAC components
- Users: These are individual users within the Harness system. One User can belong to many user groups.
For more information on creating a new User, see Add and Manage Users. - User Groups: User Groups contain multiple Harness Users. Each User Group has assigned roles. You can create User Groups at Account/Org/Project scope.
For more information on creating a new User Group, see Add and Manage User Groups. - Service Account: A Service Account is a set of API Keys with a set of permissions assigned to them via role assignment. API Keys are used for authenticating and authorizing remote services attempting to perform operations in Harness via our APIs. API Keys that are part of a Service Account are assigned permissions (equivalent to users) that Service Accounts inherit.
For more information on creating a new Service Account, see Add and Manage Service Accounts. - Resource Groups: A Resource Group is a set of Harness resources that a User or User Group can access. You can create Resource Groups at Account/Org/Project scope.
For more information on creating a new Resource Group, see Add and Manage Resource Groups. - Roles: A Role is a group of permissions you assign to a User Group. You can create roles at Account/Org/Project scope.
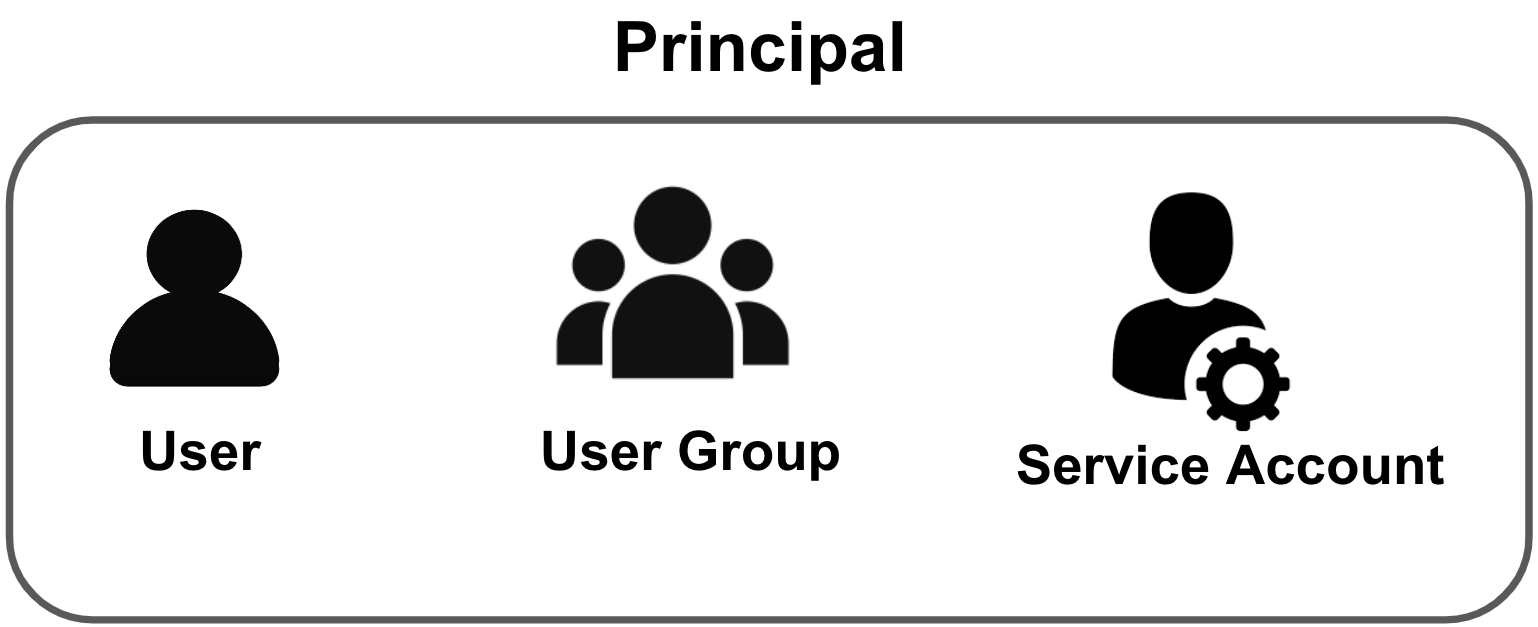
For more information on creating a new Role, see Add and Manage Roles. - Principal: A principal can be a User, User Group, or Service Account to which you provide access. Role assignments are done on any of these principals, also known as Subjects.
What can you do with RBAC?
Here are a few examples of what RBAC can be used for:
- Allow Users, User Groups, or Service Accounts to manage and access the resources through the Account/Org/Project Admin role.
- Allow Users, User Groups, or Service Accounts to view the resources through the Account/Org/Project Viewer role.
- Allow Users, User Groups, or Service Accounts to manage and access specific resources through Custom Roles.
How does RBAC work?
The way you control access to resources using RBAC is to assign permissions to users and groups to manage resources.
- Permissions that you want to assign to a User or User Group or a Service Account are grouped together in a Role.
- Resources that you want to control access to are grouped together in a Resource Group.
- An account administrator assigns a Role and Resource Group to a Principal - User or User Group or Service Account. This assignment is called Role Assignment.
- Role Assignment grants the Principal the permissions from the Role on the set of resources in the Resource Group.
RBAC scope
Harness Accounts allow you to group Organizations and Projects that share the same goal. These have their own scope of access.
In Harness, you can specify scopes at three levels:
- Account
- Organization
- Project
Scopes are structured in a parent-child relationship. You can assign roles at any of these levels of scope.
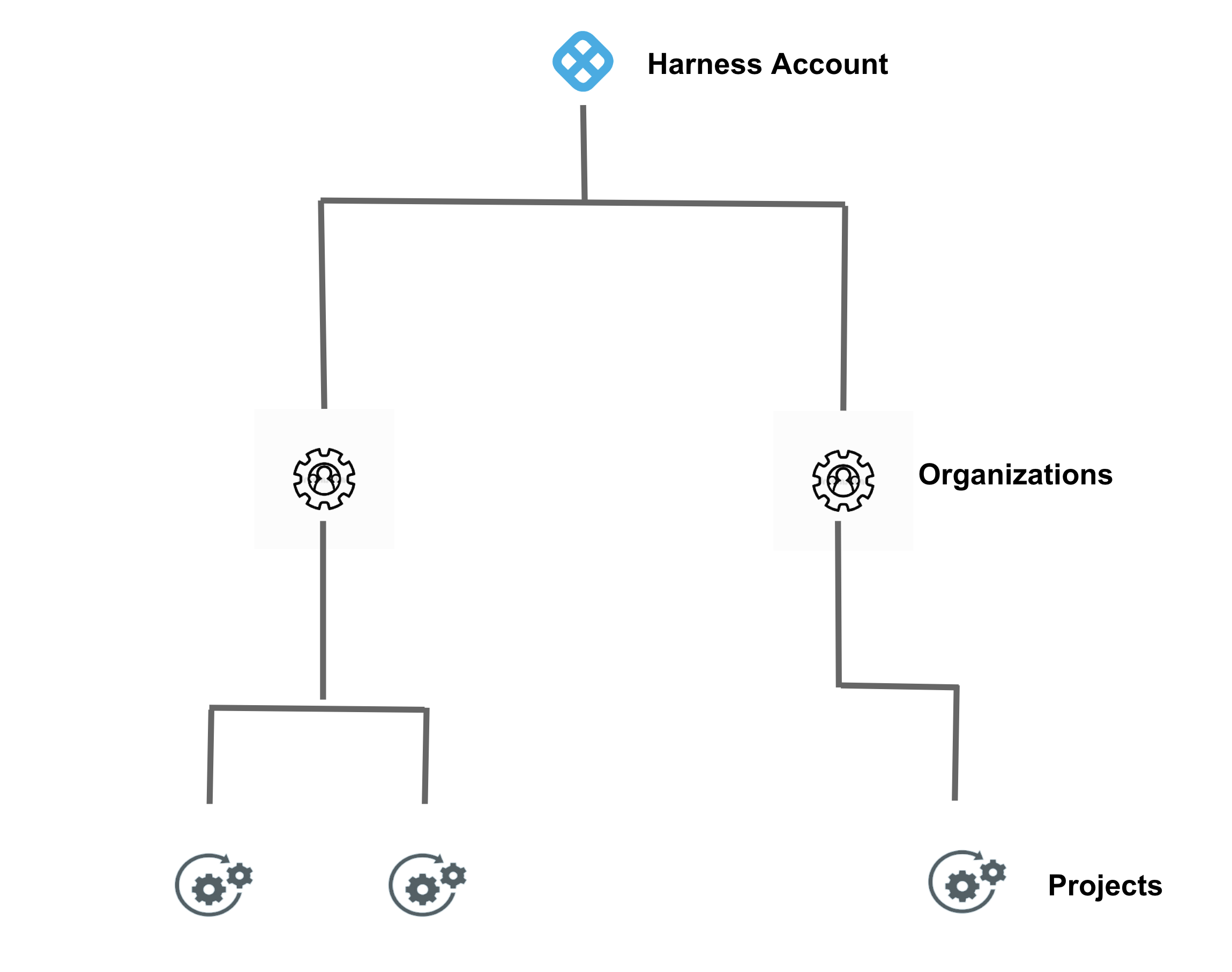 The following table shows what it means to add users and resources at different scopes or hierarchies:
The following table shows what it means to add users and resources at different scopes or hierarchies:
| Scope | When to add users? | When to add resources? |
| Account | To manage administrative functions or have total access and authority over the whole hierarchy, add them to the Account scope. | Add resources to the Account scope to allow sharing across the entire hierarchy. |
| Organization | To have visibility and control over all of the projects within this Org, add users to the Org scope. | Add resources to the Org scope to allow sharing across projects within this Org while isolating from other organizations. |
| Project | To manage or contribute to this Project, add users to the Project scope. | Add resources to the Project scope to provide total control to the Project teams. |
To know more about Organizations and Projects, see Create Organizations and Projects.
Resource group
A Resource Group is a collection of resources that are all managed by the same set of users and have the same access control policies.
Resource Groups can be of two types:
- All Resources– Collection of all the resources of a given type.
- Named Resources– Collection of a specific set of individual resources.
 Harness includes the following default Resource Groups at each scope:
Harness includes the following default Resource Groups at each scope:
| Scope | Resource Group | Description |
| Account | All Resources Including Child Scopes | Includes all resources within the Account's scope, as well as those within the scope of the Orgs and Projects within the Account. |
| Account | All Account Level Resources | Includes all resources within the Account's scope. Excludes resources that are within the scope of an Org or Project. |
| Org | All Resources Including Child Scopes | Includes all the resources within the Org's scope, as well as those within the scope of all Projects within the Org. |
| Org | All Organization Level Resources | Include all resources within the Org's scope. Excludes resources that are within the scope of a Project. |
| Project | All Project Level Resources | Includes all resources within the scope of a Project. |
You can also create custom resource groups within any scope.
For more information, see Add and Manage Resource Groups.
Role
A Role is a set of permissions that allow or deny specific operations on a specific set of resources. A Role defines access to resources within a single scope — Project/Org/Account.
Harness provides the following default roles at the Account, Org, and Project scope:
| Scope | Role |
| Account | Account Admin |
| Account | Account Viewer |
| Account | Feature Flag Manage Role |
| Org | Organization Admin |
| Org | Organization Viewer |
| Org | Feature Flag Manage Role |
| Project | Project Admin |
| Project | Project Viewer |
| Project | Pipeline Executor |
| Project | Feature Flag Manage Role |
For more information, see Add and Manage Roles.
Role assignment
A role assignment consists of the following elements:
- Principal
- Role
- Resource Group
- Scope
Following are a few key points for role assignment in Harness:
- Role Assignment is nothing but assigning a Role and a Resource Group to a Principal.
- The Principal gets access to resources through Role Assignment.
- The Principal on which role assignment is done can be an individual User, User Group, or Service Account.
- Each Principal can have multiple role assignments.
- Depending on where you wish to set up access control, you may assign roles at the Account, Org, or Project scope.
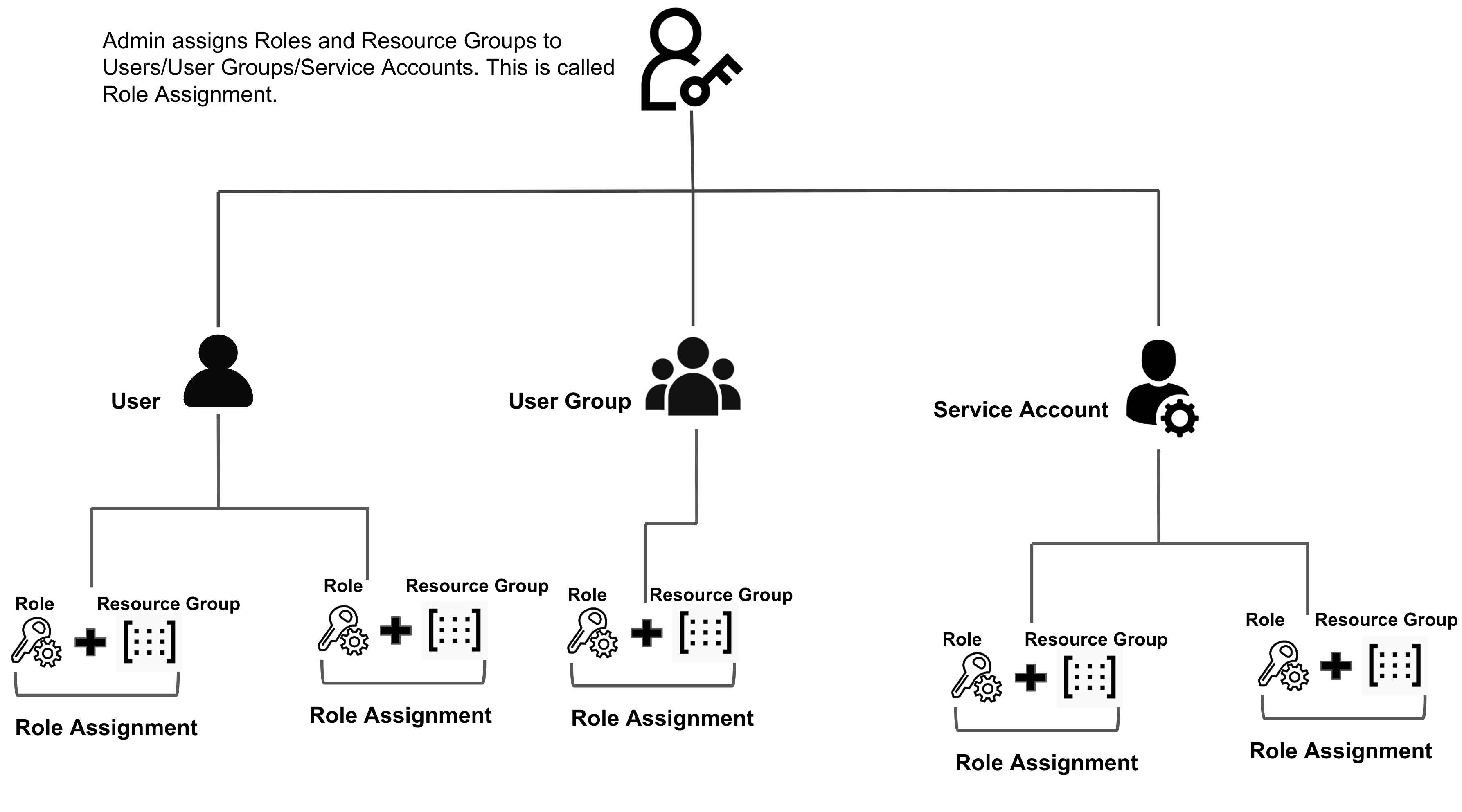
The following list explains the different role assignments with the default roles and resource groups:
| Role Assignment (Default Role + Default Resource Group) | Description |
| Account Admin + All Resources Including Child Scopes | A User Group with this role assignment has the following permissions: |
| Account Admin + All Account Level Resources | A User Group with this role assignment has the following permissions: |
| Account Viewer + All Resources Including Child Scopes | A User Group with this role assignment has the following permissions: |
| Account Viewer + All Account Level Resources | A User Group with this role assignment has the following permissions: |
| Feature Flag Manage Role + All Resources Including Child Scopes | A User Group with this role assignment has the following permissions: |
| Feature Flag Manage Role + All Account Level Resources | A User Group with this role assignment has the following permissions: |
| Organization Admin + All Resources Including Child Scopes | A User Group with this role assignment has the following permissions: |
| Organization Admin + All Organization Level Resources | A User Group with this role assignment has the following permissions: |
| Organization Viewer + All Resources Including Child Scopes | A User Group with this role assignment has the following permissions: |
| Organization Viewer + All Organization Level Resources | A User Group with this role assignment has the following permissions: |
| Feature Flag Manage Role + All Resources Including Child Scopes | A User Group with this role assignment has the following permissions: |
| Feature Flag Manage Role + All Organization Level Resources | A User Group with this role assignment has the following permissions: |
| Project Admin + All Project Level Resources | A User Group with this role assignment has the following permissions: |
| Project Viewer + All Project Level Resources | A User Group with this role assignment has the following permissions: |
| Feature Flag Manage + All Project Level Resources | A User Group with this role assignment has the following permissions: |
| Pipeline Executor + All Project Level Resources | A User Group with this role assignment has the following permissions: |
Permissions
When a Harness User is a member of multiple User Groups, the sum of all the role assignments determines the effective permissions for the user.
For example, let us consider a user with the following role assignments:
- Account Admin role for All Resources Including Child Scopes.
- Organization Viewer role for All Resources Including Child Scopes.
The sum of these role assignments is effectively the Account Admin role for All Resources Including Child Scopes. Therefore, in this case, the Organization Viewer role for All Resources Including Child Scopes has no impact.
By default, users will have View permissions for all resources at all scopes (Account/Org/Project).
Blog post
The following blog post walks you through User and Role Management in Harness:
User and Role Management in the Harness Software Delivery Platform