Linux DNS error
Linux DNS error injects chaos to disrupt the DNS resolution on a Linux machine.
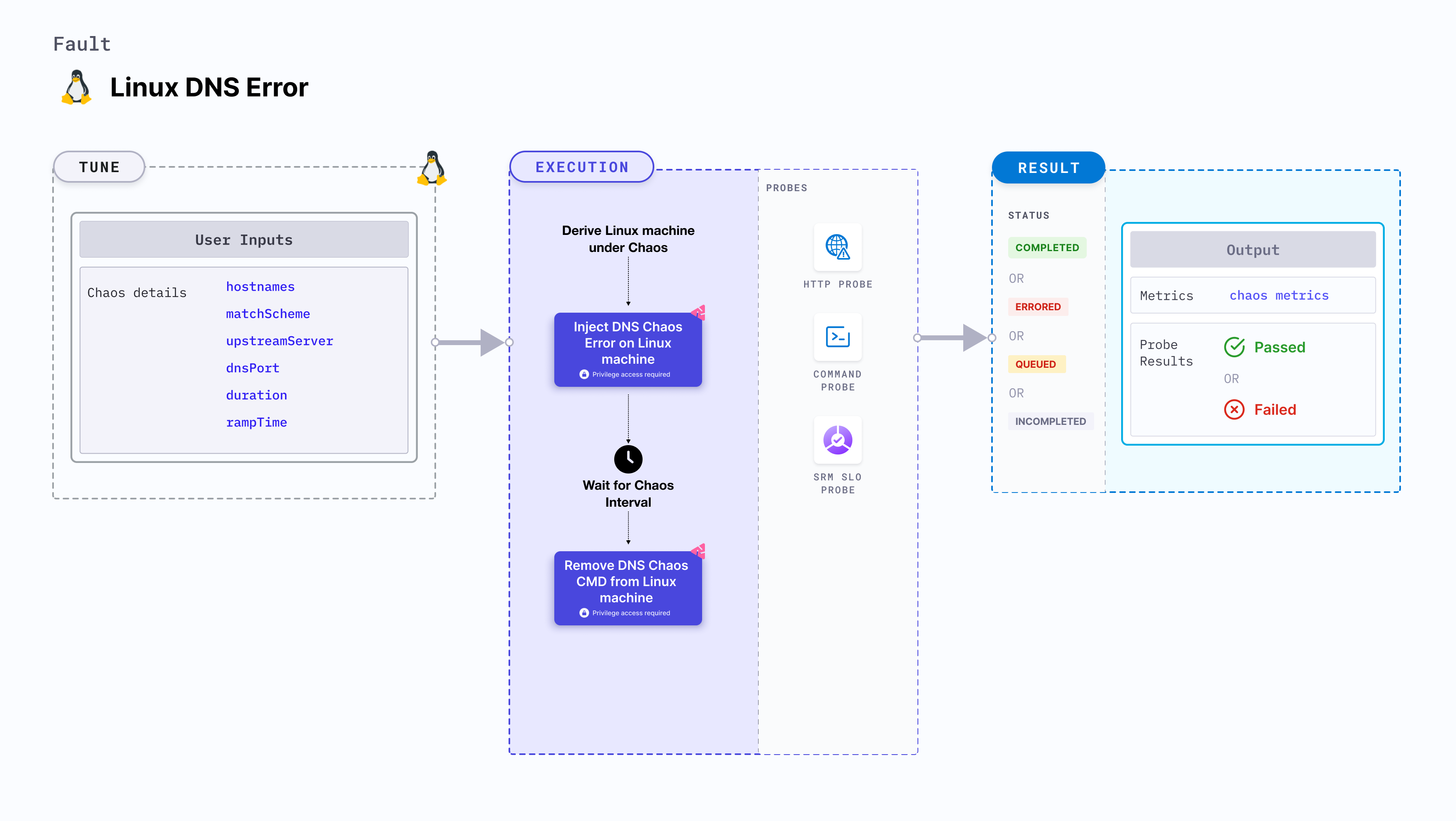
Use cases
- Induces DNS error on the target Linux machines.
- Simulates loss of access to host by blocking the DNS resolution of host names.
note
- This fault can be executed on Ubuntu 16 or higher, Debian 10 or higher, CentOS 7 or higher, RHEL 7 or higher, and openSUSE LEAP 15.4 or higher.
- The
linux-chaos-infrastructuresystemd service should be in an active state, and the infrastructure should be inCONNECTEDstate.
Fault tunables
Optional tunables
| Tunable | Description | Notes |
|---|---|---|
| hostNames | List of the target host names or keywords. For example, '["google.com","litmuschaos.io"]'. | If not provided, all host names are targeted. |
| matchScheme | Determines whether the DNS query has to exactly match one of the targets or can have any of the targets as substring. It can be exact or substring. | If not provided, it is set to exact |
| upstreamServer | URL of the DNS upstream server. | |
| dnsPort | Port of the DNS server. | |
| duration | Duration through which chaos is injected into the target resource (in seconds). | Default: 30s |
| rampTime | Period to wait before and after injecting chaos (in seconds). | Default: 0s |
Host names
The hostNames input variable subjects the comma-separated host names to chaos.
The following YAML snippet illustrates the use of this environment variable:
# target host names
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-dns-error
labels:
name: dns-error
spec:
dnsChaos/inputs:
hostNames: '["litmuschaos.io","google.com"]'
Match scheme
The matchScheme input variable either exactly matches one of the targets to the DNS query or has any of the targets as a substring of the DNS query.
The following YAML snippet illustrates the use of this environment variable:
# dns query match scheme
apiVersion: litmuchaos.io/v1alpha1
kind: LinuxFault
metadata:
name: linux-dns-error
labels:
name: dns-error
spec:
stressChaos/inputs:
matchScheme: 'exact'