Security Step Settings Reference
This topic includes the Security step settings for each of the scanner providers supported by Harness.
What's new: Improved UIs and set-up workflows for popular scanners
On March 14, 2023, Harness introduced a set of new UIs (step palettes) for Aqua Trivy, Bandit, SonarQube, and other popular scanners. These steps greatly simplify the process of setting up scans in your pipelines. Previously, the workflow for all scanners was to enter a set of hard-coded key and value strings in a Security step. These new steps have simplified user-friendly UIs that include only the options relevant to the specific scanner, mode, and target.
The following security steps are now generally available:
- Aqua Trivy (STO-5393)
- Bandit (STO-5050)
- Black Duck Hub (STO-5052)
- Checkmarx (STO-5073)
- Grype (STO-5394)
- Mend (formerly Whitesource) (STO-5392)
- Prisma Cloud (formerly Twistlock) (STO-5055)
- Snyk (STO-5053)
- SonarQube (STO-5051)
- Zed Attack Proxy (ZAP) (STO-5058)
Scanner categories
The following list shows the scan types that STO supports:
- SAST (Static Application Security Testing) scans a code repository and identifies known vulnerabilities in the proprietary code.
- SCA (Software Composition Analysis) scans a code repository and identifies known vulnerabilities in open-source libraries and packages used by the code.
- DAST (Dynamic Application Security Testing) scans a running application for vulnerabilties by simulating a malicious external actor exploiting known vulnerabilties.
- Container Scanning identifies known vulnerabilities in a Docker container.
Data ingestion methods
Harness Security Testing Orchestration integrates with multiple scanners and targets. Different types of scan approaches can be done on each scanner-target combination:
- Orchestrated (
orchestratedScan) Scans are fully orchestrated. A Security step in the Harness pipeline orchestrates a scan and then normalizes and compresses the results. - Extraction (
dataLoad) Scans are partially orchestrated. The Security step pulls scan results from an external SaaS service and then normalizes and compresses the data. - Ingestion (
ingestionOnly) Scans are not orchestrated. The Security step ingests results from a previous scan (for for a scan run in an previous step) and then normallizes and compresses the results.
The scanner, targets, and scan approach combinations are covered in the next section.
Harness STO scanner support
| Scan Mode | Open Source | Commercial |
|---|---|---|
| SAST |
|
|
| SCA |
|
|
| DAST |
| |
| Containers |
|
|
Scanner binaries used in STO container images
Harness maintains and updates a container image for every scanner supported by STO. The following table lists the binaries and versions used for the most popular scanners.
| Scanner | Binary | Current version |
|---|---|---|
| Aqua Trivy | trivy image | Latest stable build |
| Bandit | bandit | 1.7.4 |
| Black Duck Hub | synopsys detect | 7.9.0 |
| Brakeman | brakeman | 4.4.0 |
| Checkmarx | runCxConsole.sh | 1.1.18 |
| Grype | grype | Latest stable build |
| Nikto | Nikto | 2.1.6 |
| Nmap | nmap | 7.92 |
| Prowler | prowler | Latest stable build |
| SonarQube | sonar-scanner | 4.7.0.2747 |
| Twistlock | twistcli | 22.12.582 |
| Whitesource | java -jar /opt/whitesource/wss-unified-agent.jar | 22.10.1 |
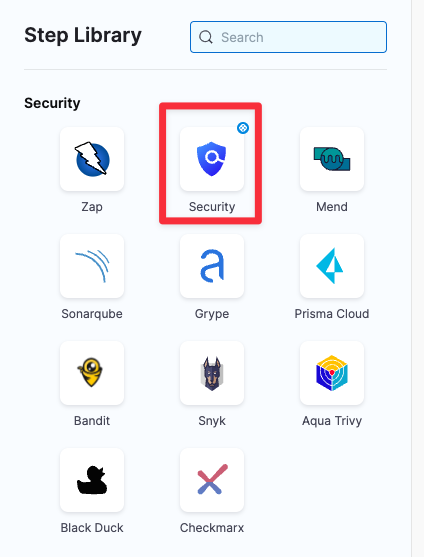
Security steps and scanner templates
The Step library includes a Security step for setting up scanners: open the step and configure the scan as a set of key/value pairs under Settings.
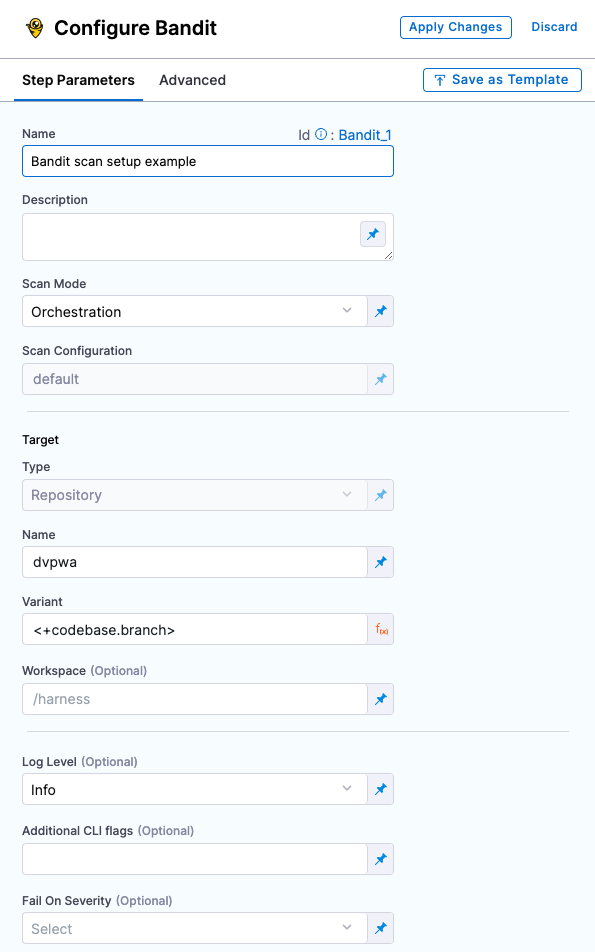
Some scanners also have scanner templates with UIs that simplify the process of setting up a scanner.
Step Library with Security step and scanner templates
Security step configuration
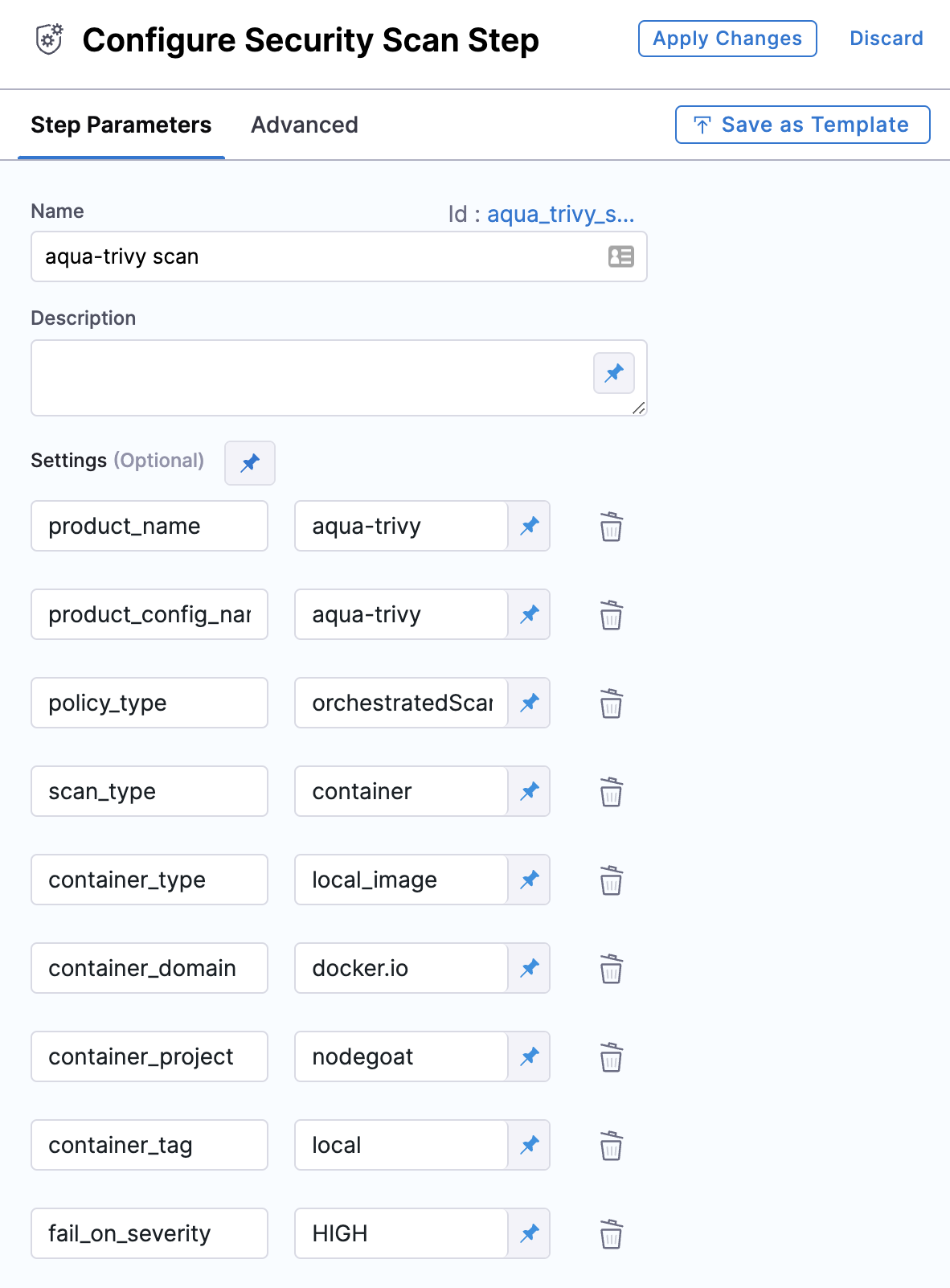
Scanner template configuration